Hello, today I will be writing a full and detailed tutorial on fully securing your computer to be safer on the internet
First Things FirstWe will first be going over the main forms of malware and spyware you can get, and what each one does:
•Keyloggers
Strokes all of your hit keys, and often sends them to a person, without your consent, via e-mail or FTP servers.
(Click here for more information)
•Remote Administration Tools/Trojans [RATs]
Remote Administration Tools, or as called by other, Remote Access Trojans, are programs that give to a hacker, full control over your computer. Many of these RATs include features such as built-in keyloggers, File Managers (to view your files), and many other malicious features that may harm you.
(click here for more information)
•Rogue Anti-Virus
A Rogue Anti-Virus is a virus which, once present on your computer, constantly and without your permission, does a "virus scan" and/or prompts you to buy the full version to be able to remove a certain virus. They also slow down your computer remarkably, to make even more people fall for the scam, believing they have many malware present. Rogue Anti-Viruses are often known to be very hard to remove once on your computer.
(click here to see a list of rogue anti-viruses you should avoid)
•Rootkits
Rootkits are by far the most damaging and hardest to remove malware. Since I find it hard to explain, I will directly quote Wikipedia below:
A rootkit is software that enables continued privileged access to a computer while actively hiding its presence from administrators by subverting standard operating system functionality or other applications. The term rootkit is a concatenation of "root" (the traditional name of the privileged account on Unix operating systems) and the word "kit" (which refers to the software components that implement the tool). The term "rootkit" has negative connotations through its association with malware.[1]
Typically, an attacker installs a rootkit on a computer after first obtaining root-level access, either by exploiting a known vulnerability or by obtaining a password (either by cracking the encryption, or through social engineering). Once a rootkit is installed, it allows an attacker to mask the ongoing intrusion and maintain privileged access to the computer by circumventing normal authentication and authorization mechanisms. Although rootkits can serve a variety of ends, they have gained notoriety primarily as malware, hiding applications that appropriate computing resources or steal passwords without the knowledge of administrators and users of affected systems. Rootkits can target firmware, a hypervisor, the kernel, or—most commonly—user-mode applications.
Rootkit detection is difficult because a rootkit may be able to subvert the software that is intended to find it. Detection methods include using an alternate, trusted operating system; behavioral-based methods; signature scanning; difference scanning; and memory dump analysis. Removal can be complicated or practically impossible, especially in cases where the rootkit resides in the kernel; reinstallation of the operating system may be the only alternative.
•Viruses
Ahh, viruses. We hear this word so often, yet only a few actually know what a real virus does. A virus is often a code found in executable form, that multiplies and copies itself on the victimized system. It easily spreads in a network, and often binds/attaches itself to other applications on the system.
(click here for more information)
With that being said, let me clarify that the malware I have mentioned are only the most common ones you may come across.
Tutorial written by Piratz0, also known as The Pickpocket or The Silent
♦How to protect yourself!♦I will now go on to explaining the various ways you can protect your system from all the dangers of the internet.
Keeping your OS up-to-date!This is the first step to having a secure computer, and is one of the most crucial part of staying protected from newly released viruses and malware.
Extra Tip: Windows XP users, get Vista or Windows 7! Xp is a great OS, but it is also the most exploit-vulnerable OS!
Have an Anti-VirusHaving an Anti-Virus is very important to keep your computer safe, since it blocks malware BEFORE it gets in.
List of some good AVs:
Avira:
Price: FREE!
Screenshot:
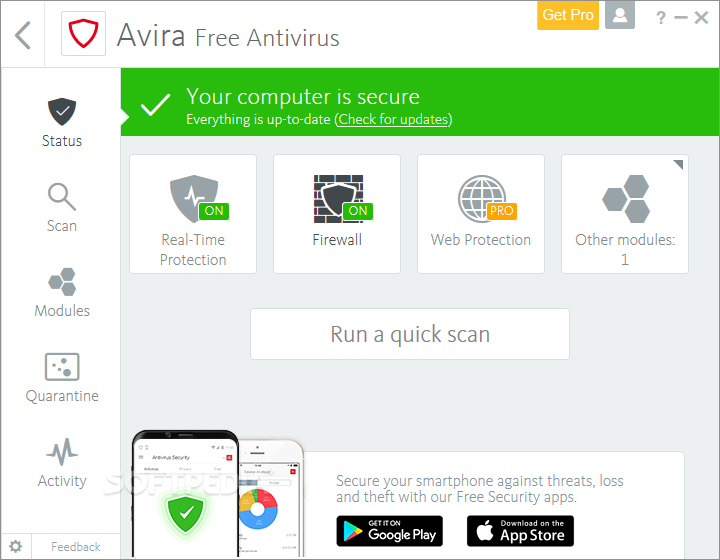
Additional information:
If you don't have virus protection, your PC will be infected with malware in a matter of minutes. Avira AntiVir Personal offers basic protection against viruses, worms, Trojans, rootkits, adware, and spyware that has been tried and tested over 100 million times worldwide. What's more, it is available free-of-charge. It not only protects against these types of malware, but offers as well, in case of an infection, the possibility of removing viruses very easily and repair the system automatically.
DL Link
.
•Kaspersky
Price: 49.95$/year
Screenshot:
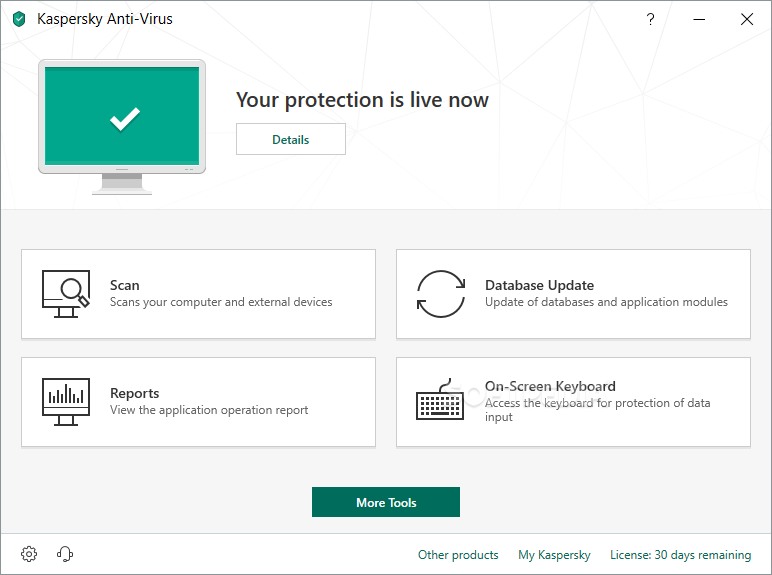
Additional information:
Kaspersky Anti-Virus combines the essential security of our advanced Anti-Virus software with additional layers of defense, such as firewall and parental controls. Innovative technologies deliver real-time protection, monitor suspicious activity, and block dangerous actions before they can cause harm - all while working silently in the background.
Features include: Up-to-the-second Internet threat protection, rootkit detection and removal, a system watcher, and a gaming mode.
DL Link
Tutorial written by Piratz0, also known as The Pickpocket or The Silent
•McAfee
Price:49.99$
Screenshot:
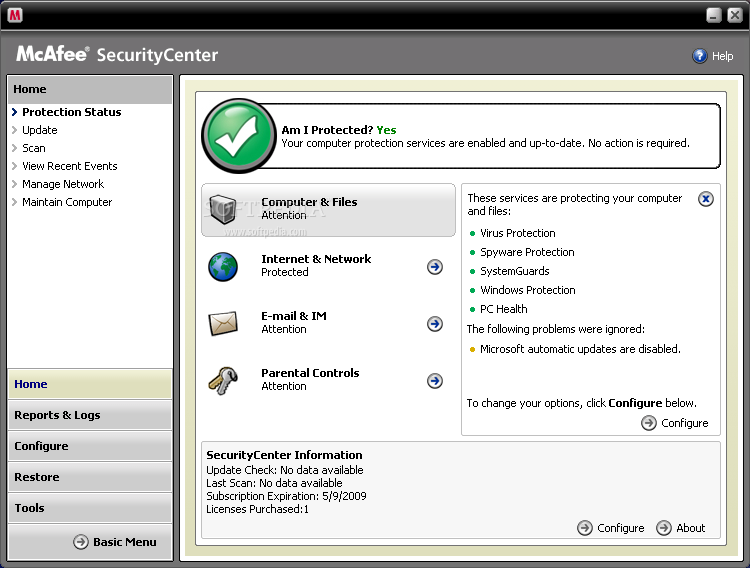
Additional information:
McAfee AntiVirus Plus 2010 offers proactive PC security to prevent malicious attacks, so you can protect what you value as well as surf, search, and download files online with confidence. McAfee SiteAdvisor's Web safety ratings help you avoid unsafe Web sites. This service also provides security against multi-pronged attacks by combining antivirus and antispyware technologies. McAfee's security service continuously delivers the latest software so your protection is never out-of-date. You can now easily add and manage security for multiple PCs in your home. Moreover, improved performance allows it to protect, without disturbing you.
DL Link
•Norton Antivirus
Price:54.99$/year
Screenshot:
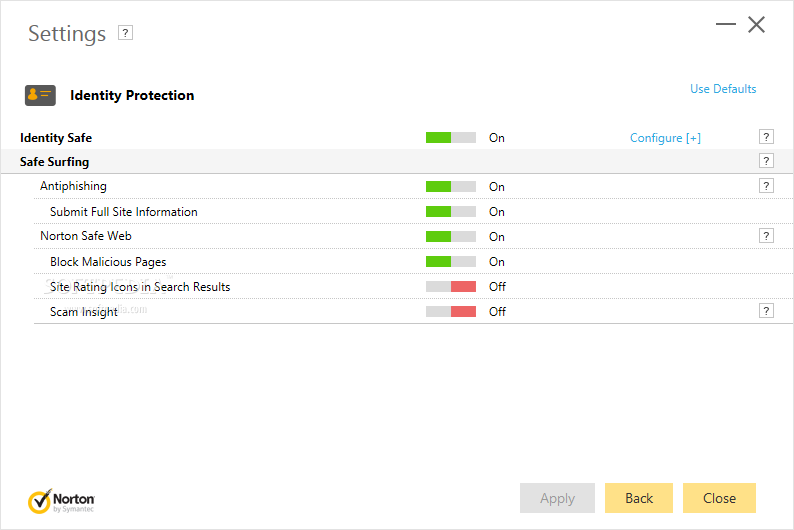
Additional information:
Norton 360 delivers all-in-one security for everything the computer users in your family care about, providing automatic and transparent protection from viruses, spyware, fraudulent Web sites, phishing scams, intrusions, and the latest online threats. With a renewable subscription, up to three PCs in your household are continuously protected, safeguarding your family when they shop or bank online, play games, send email, or download files. Norton 360 also helps keep your PCs tuned for peak performance. Plus, it protects the data on them by making it easy to automatically back up and restore important files locally or to a secure online storage service. Requires high-speed Internet access. 2 GB of online storage included, with option to purchase more.
DL Link
Continued....
Having a firewallHaving a firewall is aswell very important since it may block malicious software to connect to a hacker's computer.
There are 2 good and free firewalls out there which are:
•Comodo Firewall
Price: FREE!
Screenshot:
Additional Information:
Comodo's free Firewall is your first layer of defense against viruses, worms, Trojans, hackers and all Internet threats. Comodo's Firewall uses Default Deny Protection to prevent threats from occurring, rather than just detecting them when it's already too late. Whenever an unknown piece of software is introduced to your system, Comodo Firewall cross-references it with a white-list of over 15 million trusted files and applications. If the file asking for access is on the list, Comodo Firewall can be sure it's safe for your computer to allow it to execute. If not, Comodo Firewall will alert you that a possibly malicious file is trying to enter your PC.
DL Link
•Zonealarm Firewall
Price: FREE!
Screenshot:
Additional information:
ZoneAlarm Free Firewall blocks intruders and makes you invisible to hackers; stops attacks that antivirus and your default Windows security misses; blocks new viruses from sending your data (like passwords or social security numbers) to hackers; detects spoofed programs; stops hacking disguised as harmless network transmissions; works seamlessly with antivirus programs; works automatically--no expertise required; includes security for safer Web browsing.
DL Link
Having a Secondary ScannerA secondary scanner is, well, a scanner, that you only use when you KNOW you are infected, but your AV does not detect the malware. These scanners are usually not activated until you do a manual scan.
Tutorial written by Piratz0, also known as The Pickpocket or The Silent
My suggestion:
•Malware Byte's Anti-Malware
Price: FREE!
Screenshot:
Additional information:
Malwarebytes' Anti-Malware is a high performance anti-malware application that thoroughly removes even the most advanced malware and spyware. With one of the fastest, most effective quick scans and malware removal capabilities on the market, this program is the perfect addition to your PC's defenses.
DL Link
A KeyscramblerA keyscrambler mainly protects you from keyloggers. What it does is scramble your keyhits, so they are uncomprehendable.

